Botnet
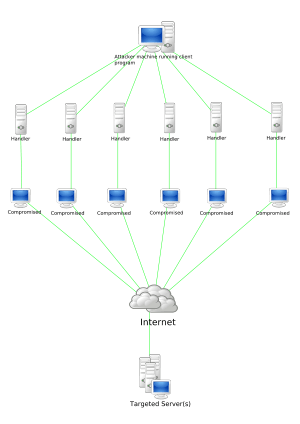
A botnet is a number of Internet-connected computers communicating with other similar machines in which components located on networked computers communicate and coordinate their actions by command and control (C&C) or by passing messages to one another (C&C might be built into the botnet as P2P).[1] Botnets have been used many times to send spam email or participate in distributed denial-of-service attacks. The word botnet is a combination of the words robot and network. The term is usually used with a negative or malicious connotation.
Applications
Legal
Most of the time when botnets are in the legal area are commonly used for Distributed computing which is a field of computer science that studies distributed systems. A distributed system is a software system in which components located on networked computers communicate and coordinate their actions by passing messages. The components interact with each other in order to achieve a common goal. Three significant characteristics of distributed systems are: concurrency of components, lack of a global clock, and independent failure of components. A command and control may be present in the distributed computing but no zombie computer is present in this type of system.[2]
Illegal
Botnets sometimes compromise computers whose security defenses have been breached and control ceded to a third party. Each such compromised device, known as a "bot", is created when a computer is penetrated by software from a malware (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols such as IRC and Hypertext Transfer Protocol (HTTP).[3]
Botnets are increasingly rented out by cyber criminals as commodities for a variety of purposes.[4]
Architecture
The methods on which botnets are built for communications. Botnet architecture evolved over time, and not all botnets exhibit the same topology for command and control. Advanced topology is more resilient to shutdown, enumeration or discovery. However, some topologies limit the marketability of the botnet to third parties. Typical botnet topologies are star, multi-server, hierarchical and random.
Client–server model

The Client–server model appeared on the first types of botnets that appeared online and has usually been built on Internet Relay Chat or by using Domains or Websites which will have the commands listed for the botnet to be controlled. In IRC commands tend to be simpler and botnets tend to be smaller if built on an IRC network. Since IRC networks require low bandwidth and use simple methods for communication, they have been used to host botnets that tend to be simple in construction and have been used many times for coordinating DDoS attacks or spam campaigns while switching channels to avoid being taken down. Blocking certain keywords has sometimes proved effective in stopping a botnet based on IRC.
Most of the largest botnets that have been built tended to use domains rather than IRC in their construction.(see Rustock botnet see also Srizbi botnet.) Almost always they have been hosted with bullet proof hosting services.(See Bulletproof hosting.) Since most of the time botnets based on the Client-server model have been taken down in a matter of time, hackers have moved toward P2P as an alternative to avoid botnet takedowns.
Botnet servers are typically redundant, linked for greater redundancy so as to reduce the threat of a takedown. Actual botnet communities usually consist of one or several controllers that rarely have highly developed command hierarchies; they rely on individual peer-to-peer relationships.[5]
The botnet server structure mentioned above has inherent vulnerabilities and problems. For example, finding one server with one botnet channel can often reveal the other servers, as well as their bots. A botnet server structure that lacks redundancy is vulnerable to at least the temporary disconnection of that server. However, recent IRC server software includes features to mask other connected servers and bots, eliminating that approach.
Peer-to-peer

Since most of the time IRC networks and Domains can be taken down with time, hackers have moved on to P2P as a way to make it harder to be taken down. Some have even been known to use encryption as a way to secure or lock down the botnet from others, most of the time when they use encryption it is Public-Key encryption and has presented challenges in both implementing it and breaking it.(See Gameover ZeuS See also ZeroAccess botnet.)
Some newer botnets are almost entirely P2P. Command and control is embedded into the botnet rather than relying on external servers, thus avoiding any single point of failure and evading many countermeasures.[6] Commanders can be identified just through secure keys, and all data except the binary itself can be encrypted. For example, a spyware program may encrypt all suspected passwords with a public key that is hard-coded into it, or distributed with the bot software. Only with the private key (known only by the botnet operators) can the data captured by the bot be read.
In the P2P method of command and control the bot only tends to know a list of peers of which it can send commands to and that are passed on to other peers further down the botnet. The list tends to be around 256 peers which allows it to be small enough for it to allow commands to be quickly passed on to other peers and makes it harder to disrupt the operation of the botnet while allowing it to remain online if major numbers of peers are taken down in a takedown effort.
Core components of a botnet
There are several core components in a botnet which have been used. The main ones are listed below
Command and control
In the field of computer security, command and control (C&C) infrastructure consists of servers and other technical infrastructure used to control malware in general, and, in particular, botnets. Command and control servers may be either directly controlled by the malware operators, or themselves run on hardware compromised by malware. Fast-flux DNS can be used as a way to make it difficult to track down the control servers, which may change from day to day. Control servers may also hop from DNS domain to DNS domain, with domain generation algorithms being used to create new DNS names for controller servers.
In some cases, computer security experts have succeeded in destroying or subverting malware command and control networks, by, among other means, seizing servers or getting them cut off from the Internet, denying access to domains that were due to be used by malware to contact its C&C infrastructure, and, in some cases, breaking into the C&C network itself. In response to this, C&C operators have resorted to using techniques such as overlaying their C&C networks on other existing benign infrastructure such as IRC or Tor, using peer-to-peer networking systems that are not dependent on any fixed servers, and using public key encryption to defeat attempts to break into or spoof the network.
Zombie computer
In computer science, a zombie computer is a computer connected to the Internet that has been compromised by a hacker, computer virus or trojan horse and can be used to perform malicious tasks of one sort or another under remote direction. Botnets of zombie computers are often used to spread e-mail spam and launch denial-of-service attacks. Most owners of zombie computers are unaware that their system is being used in this way. Because the owner tends to be unaware, these computers are metaphorically compared to zombies. A coordinated DDoS attack by multiple botnet machines also resembles a zombie horde attack.
Construction
This example illustrates how a botnet is created and used for malicious gain
- A hacker purchases or builds a Trojan and/or exploit kit and uses it to start infecting users' computers, whose payload is a malicious application—the bot.
- The bot on the infected PC logs into a particular command-and-control (C&C) server. (This allows the bot master to keep logs of how many bots are active and online.)
- The bot master may then use the bots to gather keystrokes or use form grabbing to steal online credentials and may rent out the botnet as DDoS and/or spam as a service or sell the credentials online for a profit.
- Depending on the quality and capability of the bots the value is increased or decreased.
Common features
- Most botnets currently feature distributed denial-of-service attacks in which multiple systems submit as many requests as possible to a single Internet computer or service, overloading it and preventing it from servicing legitimate requests. An example is an attack on a victim's server. The victim's server is bombarded with requests by the bots, attempting to connect to the server therefore overloading it.
- Spyware is software which sends information to its creators about a user's activities – typically passwords, credit card numbers and other information that can be sold on the black market. Compromised machines that are located within a corporate network can be worth more to the bot herder, as they can often gain access to confidential corporate information. Several targeted attacks on large corporations aimed to steal sensitive information, such as the Aurora botnet.[7]
- E-mail spam are e-mail messages disguised as messages from people, but are either advertising, annoying, or malicious.
- Click fraud occurs when the user's computer visits websites without the user's awareness to create false web traffic for personal or commercial gain.
- Bitcoin Mining has been added to some of the more recent botnets have which include bitcoin mining[8] as a feature in order to generate profits for the operator of the botnet.
The botnet controller community features a constant and continuous struggle over who has the most bots, the highest overall bandwidth, and the most "high-quality" infected machines, like university, corporate, and even government machines.[9]
Organization
While botnets are often named after the malware that created them, multiple botnets typically use the same malware, but are operated by different entities.[10]
A botnet's originator (known as a "bot herder" or "bot master") can control the group remotely, usually through IRC or Domains, and often for criminal purposes. This is known as the command-and-control (C&C). Though rare, more experienced botnet operators program command protocols from scratch. These protocols include a server program, a client program for operation, and the program that embeds the client on the victim's machine. These communicate over a network, using a unique encryption scheme for stealth and protection against detection or intrusion into the botnet.
A bot typically runs hidden and uses a covert channel (e.g. the RFC 1459 (IRC) standard, Twitter, or IM) to communicate with its C&C server. Generally, the perpetrator has compromised multiple systems using various tools (exploits, buffer overflows, as well as others; see also RPC). Newer bots can automatically scan their environment and propagate themselves using vulnerabilities and weak passwords. Generally, the more vulnerabilities a bot can scan and propagate through, the more valuable it becomes to a botnet controller community. The process of stealing computing resources as a result of a system being joined to a "botnet" is sometimes referred to as "scrumping."
To thwart detection, some botnets are scaling back in size. As of 2006, the average size of a network was estimated at 20,000 computers.[11]
Recruitment
Computers can be co-opted into a botnet when they execute malicious software. This can be accomplished by luring users into making a drive-by download, exploiting web browser vulnerabilities, or by tricking the user into running a Trojan horse program, which may come from an email attachment. This malware will typically install modules that allow the computer to be commanded and controlled by the botnet's operator. After the software is downloaded, it will call home (send a reconnection packet) to the host computer. When the re-connection is made, depending on how it is written, a Trojan may then delete itself, or may remain present to update and maintain the modules. Many computer users are unaware that their computer is infected with bots.[12]
The first botnet was first acknowledged and exposed by Earthlink during a lawsuit with notorious spammer Khan C. Smith[13] in 2001 for the purpose of bulk spam accounting for nearly 25% of all spam at the time.
Countermeasures
The geographic dispersal of botnets means that each recruit must be individually identified/corralled/repaired and limits the benefits of filtering. Some botnets use free DNS hosting services such as DynDns.org, No-IP.com, and Afraid.org to point a subdomain towards an IRC server that harbors the bots. While these free DNS services do not themselves host attacks, they provide reference points (often hard-coded into the botnet executable). Removing such services can cripple an entire botnet. Some botnets implement custom versions of well-known protocols. The implementation differences can be used for detection of botnets. For example, Mega-D features a slightly modified SMTP protocol implementation for testing spam capability. Bringing down the Mega-D's SMTP server disables the entire pool of bots that rely upon the same SMTP server.[14]
Computer and network security companies have released software to counter botnets. Norton AntiBot was aimed at consumers, but most target enterprises and/or ISPs. Host-based techniques use heuristics to identify bot behavior that has bypassed conventional anti-virus software. Network-based approaches tend to use the techniques described above; shutting down C&C servers, nullrouting DNS entries, or completely shutting down IRC servers. BotHunter is software, developed with support from the U.S. Army Research Office, that detects botnet activity within a network by analysing network traffic and comparing it to patterns characteristic of malicious processes.
Some botnets are capable of detecting and reacting to attempts to investigate them, reacting perhaps with a DDoS attack on the IP address of the investigator.
Researchers at Sandia National Laboratories are analyzing botnets' behavior by simultaneously running one million Linux kernels—a similar scale to a botnet—as virtual machines on a 4,480-node high-performance computer cluster to emulate a very large network, allowing them to watch how botnets work and experiment with ways to stop them.[15]
Historical list of botnets
| Date created | Date dismantled | Name | Estimated no. of bots | Spam capacity (bn/day) | Aliases |
|---|---|---|---|---|---|
| 2004 (Early) | Bagle | 230,000[16] | 5.7 | Beagle, Mitglieder, Lodeight | |
| Marina Botnet | 6,215,000[16] | 92 | Damon Briant, BOB.dc, Cotmonger, Hacktool.Spammer, Kraken | ||
| Torpig | 180,000[17] | Sinowal, Anserin | |||
| Storm | 160,000[18] | 3 | Nuwar, Peacomm, Zhelatin | ||
| 2006 (around) | 2011 (March) | Rustock | 150,000[19] | 30 | RKRustok, Costrat |
| Donbot | 125,000[20] | 0.8 | Buzus, Bachsoy | ||
| 2007 (around) | Cutwail | 1,500,000[21] | 74 | Pandex, Mutant (related to: Wigon, Pushdo) | |
| 2007 | Akbot | 1,300,000[22] | |||
| 2007 (March) | 2008 (November) | Srizbi | 450,000[23] | 60 | Cbeplay, Exchanger |
| Lethic | 260,000[16] | 2 | none | ||
| 2007 (September) | dBot | 10,000+ (Europe) | dentaoBot, d-net, SDBOT | ||
| Xarvester | 10,000[16] | 0.15 | Rlsloup, Pixoliz | ||
| 2008 (around) | Sality | 1,000,000[24] | Sector, Kuku | ||
| 2008 (around) | 2009-Dec | Mariposa | 12,000,000[25] | ||
| 2008 (November) | Conficker | 10,500,000+[26] | 10 | DownUp, DownAndUp, DownAdUp, Kido | |
| 2008 (November) | 2010 (March) | Waledac | 80,000[27] | 1.5 | Waled, Waledpak |
| Maazben | 50,000[16] | 0.5 | None | ||
| Onewordsub | 40,000[28] | 1.8 | |||
| Gheg | 30,000[16] | 0.24 | Tofsee, Mondera | ||
| Nucrypt | 20,000[28] | 5 | Loosky, Locksky | ||
| Wopla | 20,000[28] | 0.6 | Pokier, Slogger, Cryptic | ||
| 2008 (around) | Asprox | 15,000[29] | Danmec, Hydraflux | ||
| Spamthru | 12,000[28] | 0.35 | Spam-DComServ, Covesmer, Xmiler | ||
| 2008 (around) | Gumblar | ||||
| 2009 (May) | November 2010 (not complete) | BredoLab | 30,000,000[30] | 3.6 | Oficla |
| 2009 (Around) | 2012-07-19 | Grum | 560,000[31] | 39.9 | Tedroo |
| Mega-D | 509,000[32] | 10 | Ozdok | ||
| Kraken | 495,000[33] | 9 | Kracken | ||
| 2009 (August) | Festi | 250,000[34] | 2.25 | Spamnost | |
| 2010 (January) | LowSec | 11,000+[16] | 0.5 | LowSecurity, FreeMoney, Ring0.Tools | |
| 2010 (around) | TDL4 | 4,500,000[35] | TDSS, Alureon | ||
| Zeus | 3,600,000 (US only)[36] | Zbot, PRG, Wsnpoem, Gorhax, Kneber | |||
| 2010 | (Several: 2011, 2012) | Kelihos | 300,000+ | 4 | Hlux |
| 2011 or earlier | 2015-02 | Ramnit | 3,000,000[37] | ||
| 2012 (Around) | Chameleon | 120,000[38] | None | ||
| 2016 (August) | Mirai (malware) | 380,000 | None |
- Researchers at the University of California, Santa Barbara took control of a botnet that was six times smaller than expected. In some countries, it is common that users change their IP address a few times in one day. Estimating the size of the botnet by the number of IP addresses is often used by researchers, possibly leading to inaccurate assessments.[39]
See also
- Anti-spam techniques (e-mail)
- Backdoor:Win32.Hupigon
- Carna botnet
- Command and control (malware)
- Computer worm
- E-mail address harvesting
- E-mail spam
- List poisoning
- Spambot
- Spamtrap
- Timeline of computer viruses and worms
- Xor DDoS
- Zombie (computer science)
- ZeroAccess botnet
References
- ↑ "botnet". Retrieved 9 June 2016.
- ↑ "Forensics and Incident Response". www.peerlyst.com. Retrieved 3 April 2016.
- ↑ Ramneek, Puri (2003-08-08). "Bots &; Botnet: An Overview" (PDF). SANS Institute. Retrieved 12 November 2013.
- ↑ Danchev, Dancho (11 October 2013). "Novice cyberciminals offer commercial access to five mini botnets". Retrieved 28 June 2015.
- ↑ "what is a Botnet trojan?". DSL Reports. Retrieved 7 April 2011.
- ↑ Wang, Ping et al. (2010). "Peer-to-peer botnets". In Stamp, Mark & Stavroulakis, Peter. Handbook of Information and Communication Security. Springer. ISBN 9783642041174.
- ↑ "Operation Aurora — The Command Structure". Damballa.com. Archived from the original on 11 June 2010. Retrieved 30 July 2010.
- ↑ "Bitcoin Mining". BitcoinMining.com. Archived from the original on 30 April 2016. Retrieved 30 April 2016.
- ↑ "Trojan horse, and Virus FAQ". DSLReports. Retrieved 7 April 2011.
- ↑ Many-to-Many Botnet Relationships, Damballa, 8 June 2009.
- ↑ "Hackers Strengthen Malicious Botnets by Shrinking Them" (PDF). Computer; News Briefs. IEEE Computer Society. April 2006. doi:10.1109/MC.2006.136. Retrieved 12 November 2013.
The size of bot networks peaked in mid-2004, with many using more than 100,000 infected machines, according to Mark Sunner, chief technology officer at MessageLabs.The average botnet size is now about 20,000 computers, he said.
- ↑ Teresa Dixon Murray. "Banks can't prevent cyber attacks like those hitting PNC, Key, U.S. Bank this week". Cleveland.com. Retrieved 2 September 2014.
- ↑ Credeur, Mary. "Atlanta Business Chronicle, Staff Writer". bizjournals.com. Retrieved 22 July 2002.
- ↑ C.Y. Cho, D. Babic, R. Shin, and D. Song. Inference and Analysis of Formal Models of Botnet Command and Control Protocols, 2010 ACM Conference on Computer and Communications Security.
- ↑ "Researchers Boot Million Linux Kernels to Help Botnet Research". IT Security & Network Security News. 2009-08-12. Retrieved 23 April 2011.
- 1 2 3 4 5 6 7 "Symantec.cloud | Email Security, Web Security, Endpoint Protection, Archiving, Continuity, Instant Messaging Security" (PDF). Messagelabs.com. Retrieved 2014-01-30.
- ↑ Chuck Miller (2009-05-05). "Researchers hijack control of Torpig botnet". SC Magazine US. Retrieved 10 November 2011.
- ↑ "Storm Worm network shrinks to about one-tenth of its former size". Tech.Blorge.Com. 2007-10-21. Retrieved 30 July 2010.
- ↑ Chuck Miller (2008-07-25). "The Rustock botnet spams again". SC Magazine US. Retrieved 30 July 2010.
- ↑ Stewart, Joe. "Spam Botnets to Watch in 2009". Secureworks.com. SecureWorks. Retrieved 9 March 2016.
- ↑ "Pushdo Botnet — New DDOS attacks on major web sites — Harry Waldron — IT Security". Msmvps.com. 2010-02-02. Retrieved 30 July 2010.
- ↑ "New Zealand teenager accused of controlling botnet of 1.3 million computers". The H security. 2007-11-30. Retrieved 12 November 2011.
- ↑ "Technology | Spam on rise after brief reprieve". BBC News. 2008-11-26. Retrieved 24 April 2010.
- ↑ "Sality: Story of a Peer-to-Peer Viral Network" (PDF). Symantec. 2011-08-03. Retrieved 12 January 2012.
- ↑ "How FBI, police busted massive botnet". theregister.co.uk. Retrieved 3 March 2010.
- ↑ "Calculating the Size of the Downadup Outbreak — F-Secure Weblog : News from the Lab". F-secure.com. 2009-01-16. Retrieved 24 April 2010.
- ↑ "Waledac botnet 'decimated' by MS takedown". The Register. 2010-03-16. Retrieved 23 April 2011.
- 1 2 3 4 Gregg Keizer (2008-04-09). "Top botnets control 1M hijacked computers". Computerworld. Retrieved 23 April 2011.
- ↑ "Botnet sics zombie soldiers on gimpy websites". The Register. 2008-05-14. Retrieved 23 April 2011.
- ↑ "Infosecurity (UK) - BredoLab downed botnet linked with Spamit.com". .canada.com. Retrieved 10 November 2011.
- ↑ "Research: Small DIY botnets prevalent in enterprise networks". ZDNet. Retrieved 30 July 2010.
- ↑ Warner, Gary (2010-12-02). "Oleg Nikolaenko, Mega-D Botmaster to Stand Trial". CyberCrime & Doing Time. Retrieved 6 December 2010.
- ↑ "New Massive Botnet Twice the Size of Storm — Security/Perimeter". DarkReading. Retrieved 30 July 2010.
- ↑ Kirk, Jeremy (Aug 16, 2012). "Spamhaus Declares Grum Botnet Dead, but Festi Surges". PC World.
- ↑ "Cómo detectar y borrar el rootkit TDL4 (TDSS/Alureon)". kasperskytienda.es. 2011-07-03. Retrieved 11 July 2011.
- ↑ "America's 10 most wanted botnets". Networkworld.com. 2009-07-22. Retrieved 10 November 2011.
- ↑ http://phys.org/news/2015-02-eu-police-malicious-network.html
- ↑ "Discovered: Botnet Costing Display Advertisers over Six Million Dollars per Month". Spider.io. 2013-03-19. Retrieved 21 March 2013.
- ↑ Espiner, Tom (2011-03-08). "Botnet size may be exaggerated, says Enisa | Security Threats | ZDNet UK". Zdnet.com. Retrieved 10 November 2011.
External links
- The Honeynet Project & Research Alliance, "Know your Enemy: Tracking Botnets".
- The Shadowserver Foundation - An all volunteer security watchdog group that gathers, tracks, and reports on malware, botnet activity, and electronic fraud.
- NANOG Abstract: Botnets - John Kristoff's NANOG32 Botnets presentation.
- Mobile botnets - An economic and technological assessment of mobile botnets.
- Lowkeysoft - Intrusive analysis of a web-based proxy botnet (including administration screenshots).
- EWeek.com - Is the Botnet Battle Already Lost?.
- Attack of the Bots at Wired
- Dark Reading - Botnets Battle Over Turf.
- ATLAS Global Botnets Summary Report - Real-time database of malicious botnet command and control servers.
- FBI LAX Press Release DOJ - FBI April 16, 2008
- Milcord Botnet Defense - DHS-sponsored R&D project that uses machine learning to adaptively detect botnet behavior at the network-level
- A Botnet by Any Other Name - SecurityFocus column by Gunter Ollmann on botnet naming.
- Botnet Bust - SpyEye Malware Mastermind Pleads Guilty, FBI
- LOIC IRC-0 - An Open-Source IRC Botnet for Network Stress Testing
- LOIC SLOW IRC - An Open-Source Botnet With Webpages and IRC as C&C